- Products & Services
- Free Tools
- Pricing
- Resources
- About Us
- Contact Us
- Account Login
Social engineering is the art of manipulating, influencing, or deceiving you in order to gain control over your computer system. The hacker might use the phone, email, snail mail or direct contact to gain illegal access. Phishing, spear phishing, and CEO Fraud are all examples.
OK, so who are these people? It could be a hacker in the USA who is out to do damage or disrupt. It could be a member of an Eastern Europe cybercrime mafia that is trying to penetrate your network and steal cash from your online bank account. Or, it could be a Chinese hacker that is trying to get in your organization’s network for corporate espionage.
Understanding the different attack vectors for this type of crime is key when it comes to prevention. This is how cybercriminals do it:
An invented scenario is used to engage a potential victim to try and increase the chance that the victim will bite. It's a false motive usually involving some real knowledge of the victim (e.g. date of birth, Social Security number, etc.) in an attempt to get even more information.
A 'con' exercised by professional thieves, usually targeted at a transport or courier company. The objective is to trick the company into making the delivery somewhere other than the intended location.
The process of attempting to acquire sensitive information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity using bulk email which tries to evade spam filters. Emails claiming to be from popular social websites, banks, auction sites, or IT administrators are commonly used to lure the unsuspecting public. It’s a form of criminally fraudulent social engineering.
A small, focused, targeted attack via email on a particular person or organization with the goal to penetrate their defenses. The spear phishing attack is done after research on the target and has a specific personalized component designed to make the target do something against their own interest. Here is more about how they do it.
This technique takes advantage of websites people regularly visit and trust. The attacker will gather information about a targeted group of individuals to find out what those websites are, then test those websites for vulnerabilities. Over time, one or more members of the targeted group will get infected and the attacker can gain access to the secure system.
Baiting means dangling something in front of a victim so that they take action. It can be through a peer-to-peer or social networking site in the form of a (porn) movie download or it can be a USB drive labeled “Q1 Layoff Plan” left out in a public place for the victim to find. Once the device is used or malicious file is downloaded, the victim’s computer is infected allowing the criminal to take over the network.
Latin for 'something for something', in this case it's a benefit to the victim in exchange for information. A good example is hackers pretending to be IT support. They will call everyone they can find at a company to say they have a quick fix and "you just need to disable your AV". Anyone that falls for it gets malware like ransomware installed on their machine.
A method used by social engineers to gain access to a building or other protected area. A tailgater waits for an authorized user to open and pass through a secure entry and then follows right behind.
A trick that makes men interact with a fictitious attractive female online. From old spy tactics where a real female was used.
Also deception software, rogue scanner software, or fraudware, scareware, is a form of computer malware that deceives or misleads users into paying for the fake or simulated removal of malware. Scareware, in recent years, has become a growing and serious security threat in desktop computing.
Find out what percentage of your employees are vulnerable to social engineering attacks with your free phishing security test. Plus, see how you stack up against your peers with the new phishing Industry Benchmarks!
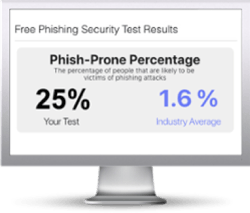
Here's how it works:
The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
You may have heard of Norton antivirus, published by Symantec. The technical director of Symantec Security Response said that threat actors are generally not trying to exploit technical vulnerabilities in Windows. They are going after you instead. “You don’t need as many technical skills to find one person who might be willing, in a moment of weakness, to open up an attachment that contains malicious content.” Only about 3% of the malware they run into tries to exploit a technical flaw. The other 97% is trying to trick a user through some type of social engineering scheme. This means it does not matter if your workstation is a PC or a Mac. The last line of defense is… you guessed it: YOU!
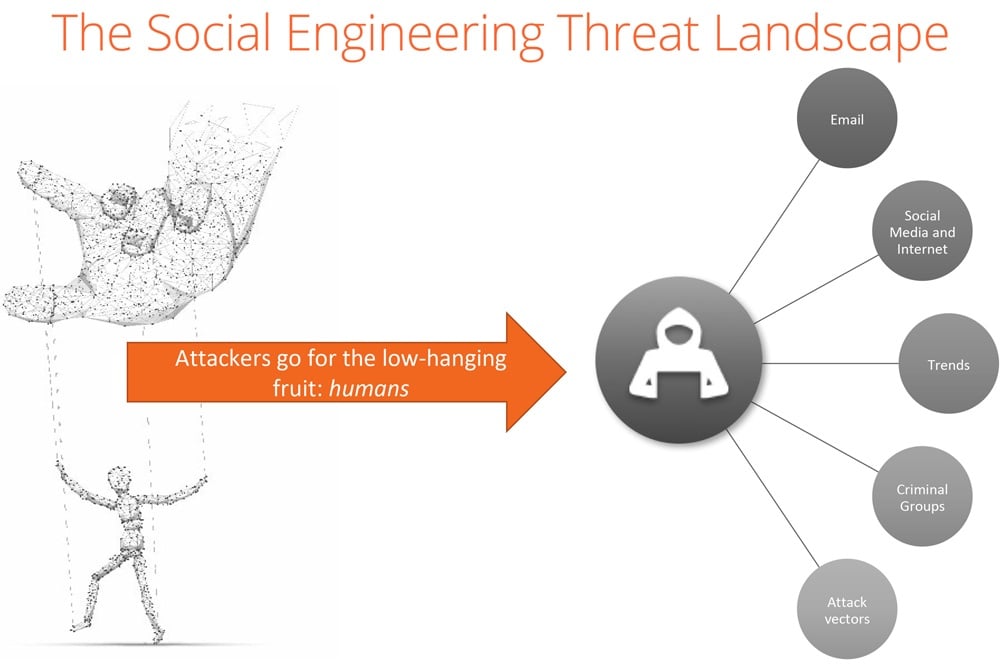
Examples of each factor in the threat landscape:
Social Media and Internet
• ReconnaissanceTrends
• RansomwareCriminal Groups
• Malicious insidersAttack Vectors
• Physical on-site attacksA classic example is the tech support scam, and it comes in many varieties and levels of sophistication.
Over the past few years online service providers have been proactively messaging customers when they detect unusual activity on their users' accounts. Not surprisingly, cybercriminals have used this trend to their advantage. Many of the emails are designed poorly with bad grammar, etc. but others look legitimate enough for someone to click if they weren't paying close attention.
Consider this fake Paypal security notice warning potential marks of "unusual log in activity" on their accounts:
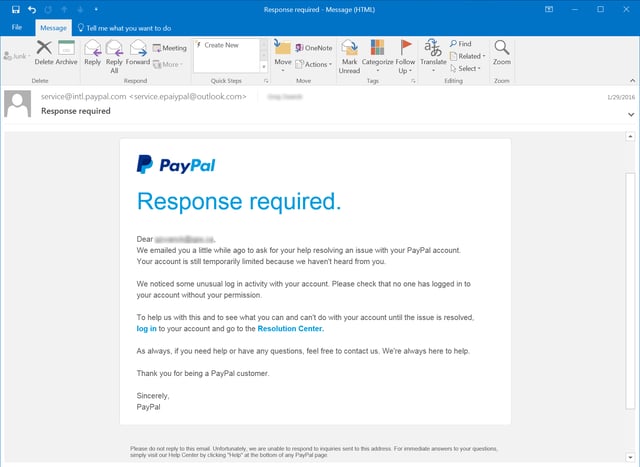
Hovering over the links would be a dead giveaway that this is a phishing email, but enough targeted users click without thinking and scams like this continue.
In a spear phishing attack, threat actors use a deep knowledge of the potential victims to target them, and that approach allows them to tailor the attack. These emails are more convincing and harder to detect than regular phishing emails. The attacker knows exactly who and what they're targeting.
Unlike mass phishing emails which may be attempting to distribute ransomware or gather individual login credentials to make a quick buck, spear phishers are normally after confidential information, business secrets, etc.
Here's an example of a CEO fraud attempt targeted at a KnowBe4 customer. She received an email from an individual purporting to be the president of the company. The employee initially responded, then remembered her training and reported the email via our Phish Alert Button, alerting her IT department to the fraud attempt.
When the employee failed to proceed with the wire transfer, she got another email from the threat actors, who probably thought they had her fooled:
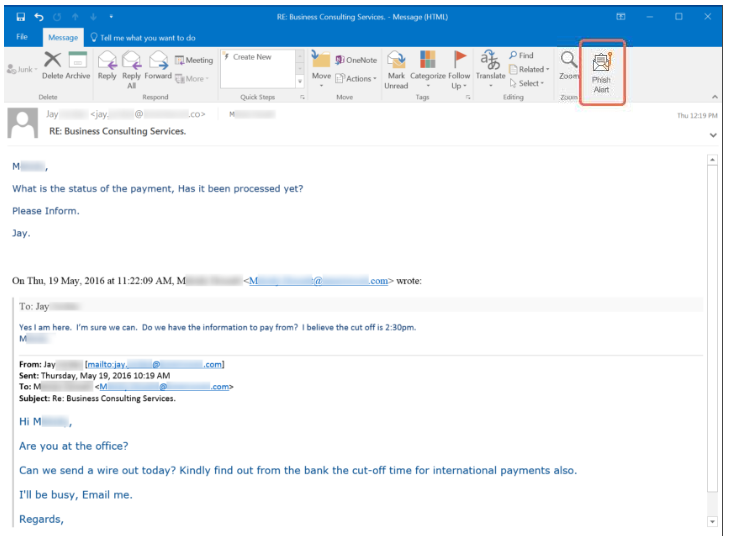
Because this employee had gone through proper security awareness training, she was able to keep her company out of the headlines. This was a close call though, and not everyone is that lucky!
Cybercriminals create bogus profiles on social media and try to trick you. They will impersonate a celebrity or one of your friends or colleagues. These profiles look very much like the real thing, and it’s easy to get tricked. They try to impersonate a celebrity that the cybercriminals already know you like a lot.
Let’s say you were tricked into believing a bogus Social Network profile. The next step is that they try to make you click on a link or install malicious software, often something to watch a video or review photos. If you click, or do that install, it’s highly likely you will infect your desktop with malware that allows the attacker to take over your PC.
We've pulled together some resources to help you defend against social engineering attacks. A good place to start is ensure you have all levels of defense in depth in place. Keep reading below to find out how you can make yourself a hard target, get additional content for yourself and your users and stay up to date with social engineering in the news via our blog.
Social engineering attacks, including ransomware, business email compromise and phishing, are problems that can never be solved, but rather only managed via a continued focus on security awareness training. Watch this video interview with Stu Sjouwerman as he explains why this is an ongoing problem and the steps required to manage it:

Researchers at IBM X-Force are monitoring several ongoing phishing campaigns by the Russian state-sponsored threat actor ITG05 (also known as “APT28” or “Fancy Bear”). APT28 has been tied to Russia’s military intelligence agency, the GRU.
© KnowBe4, Inc. All rights reserved. | Legal | Privacy Policy | Terms of Use | Security Statement | Sitemap