- Products & Services
- Free Tools
- Pricing
- Resources
- About Us
- Contact Us
- Account Login

Security awareness training is a form of education that seeks to equip employees of an organization with the information they need to protect themselves and their organization's assets from loss or harm. For the purposes of any security awareness training discussion, members of an organization include employees, temps, contractors, and anybody else who performs authorized functions online for an organization.
Organizations that must comply with industry regulations or frameworks such as PCI (Payment Card Initiative), HIPAA (Health Insurance Portability and Accountability Act of 1996), the Sarbanes-Oxley reporting requirements, NIST or ISO usually deliver security awareness training to all employees once or perhaps twice a year.
And even though it may not be required by Small and Medium Enterprises for compliance reasons, they can also benefit from training their employees to avoid cyberheists through phishing attacks, account takeovers, or other well-known means that cybercriminals use to misappropriate company funds.
To be aware, you need to be able to confront (face things as they are). KnowBe4 helps employees confront the fact that cybercriminals are trying to trick them. Once they confront that, they become aware and able to detect these scam emails and can take appropriate action like deleting the email or not clicking a link.
Cybercrime is moving at light speed. A few years ago, cybercriminals used to specialize in identity theft, but now they take over your organization’s network, hack into your bank accounts, and steal tens or hundreds of thousands of dollars. Organizations of every size and type are at risk. Are you the next cyber-heist victim? You really need a strong human firewall as your last line of defense.
In your fight against phishing and ransomware you can now deploy the best-in-class phishing platform combined with the world's largest library of security awareness training content; including 1000+ interactive modules, videos, games, posters and newsletters.
You can get access to our ModStore Preview Portal to see our full library of security awareness content; you can browse, search by title, category, language or content topics.
Preview the ModStore Now!
KnowBe4 has been named a Leader in The Forrester Wave™: Security Awareness and Training Solutions, Q1 2022. Using a 30-criteria evaluation, the Forrester Wave report ranks 11 vendors in the security awareness and training market based on their current offering, strategy and market presence. KnowBe4 received the highest scores possible in 16 of the 30 evaluation criteria, including breadth of content coverage, security culture measurement, and customer support and success.
Here's a sobering truth: Your cyber awareness program and content are the visible ‘face’ of your department to the rest of the organization. Especially if you are in a larger organization, a good portion of your coworkers don't know you, they only know what your department produces. For that reason, it HAS to be as good or better than anything else the organization is doing. Otherwise, security is seen as 'other', unimportant, an afterthought.
Learning doesn't just happen at one point in time, we need to think about the entire context of user experience. Consider this 70:20:10 model for learning and development:

The Five Moments of Need
Think About Learner Profiles/Segments Where Possible
The types of information and cultures of different departments vary. You need powerful ways to split your user population into groups. This allows you to measure them and train them in ways that best resonate with their individual needs and learning styles.
"3 truths about human nature. We’re lazy, social, and creatures of habit. Design products for this reality." - BJ Fogg, Behavioral Researcher
The Four Stages of Competence
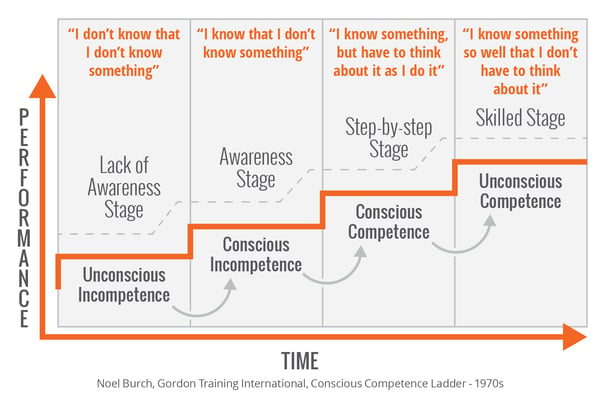
The problem is that traditional programs fail by leaving employee to linger in stages 1 and 2. Design your program to push them all the way through to stage 4. Getting users to stage 4 with constant training and simulation is ideal and cultivates the kind of behavior that can protect you from a breach.
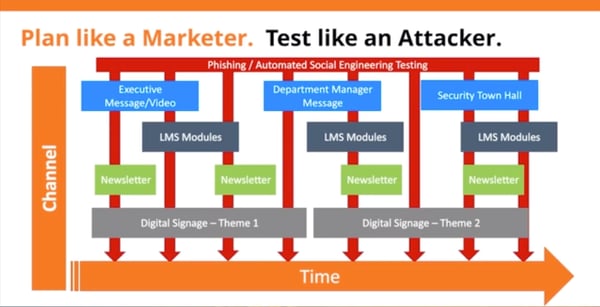
Plan like a Marketer. Test like an Attacker.
Multi channel campaign - different types of content at different times targeting different audiences going through different channels so you have a constant barrage of information and working within the context that those different people are in. You need to be constantly building reflexes and building muscle memory for your people, which is where the testing component comes in. No matter which tool you use, even if you are using a homegrown program, you need to send a social engineering test like a phishing test to users at least every 30 days. By doing both training and testing, you are running a hearts and minds campaigns like a marketer would. Over a period of time through different channels/mediums you can start building influence in the mind. Supplementing that with frequent phishing attacks you are building the muscle memory on top of that so users naturally react in the right way. That's the key to building resilience.
This whitepaper will help break down the critical components of a successful security awareness program and connect them together into something comprehensive, continuous and engaging.
Like any cyber risk mitigation strategy, security awareness training works best when procedures are written down to ensure your team walks through the necessary steps as efficiently as possible. Download this free guide to learn why a dedicated security awareness training policy is important and how to craft one that works for your organization.
More than just formal training
When you think of cyber security awareness training content, the first thing that comes to mind is probably traditional courses in an LMS. It's so much more than that! Other examples include videos, games, blog, webinars, posters, messaging on swag, self-produced content, newsletters, email content, etc. Anything you can deliver that conveys your message and elicits some kind of thinking, engagement or reaction is considered content.
Make your content interesting and relevant to your uses
This is important when it comes to training because if content isn’t appealing to the audience it’s in front of, it doesn’t feel relevant to them and won’t stick with them. Relevance is key. The human mind learns through storytelling, security awareness training is no different. A story contains contextual information that a boring, written policy simply cannot. People learn in many different ways and naturally gravitate toward different types of content, so it makes sense that if you use a one-dimensional approach in training, you are going to lose a huge part of your audience. You want to come to the learner with content suited for them rather than try to make them learn in one certain way.
And don’t just add more content for the sake of having more content. A diverse portfolio of different types of content will get the message to resonate. Repetition is key for knowledge to stick, and you need to have variety to go along with a repetitive message. Showing the same exact course over and over isn’t going to make much of a difference. If you're not sure where to begin, you're not alone. Many vendors can provide recommendations and best practices. Start there and adjust over time according to what works for your environment.
The Inside Man is KnowBe4’s first custom network-quality video series that delivers an entertaining movie-like experience for your users and makes learning how to make smarter security decisions fun and engaging. From social engineering and passwords, to social media and travel, The Inside Man reveals how easy it can be for an outsider to penetrate your organization’s security controls and network.
Want access to all five seasons and check out all our great security awareness training content?
It’s easy! You can now get access to our ModStore Preview Portal to see the world's largest library of security awareness content; including 1000+ interactive modules, videos, games, posters, and newsletters. You can easily browse, search by title, category, language or content topics. See how entertaining security awareness training can be!
Okta, one of the largest Identity Management players, provides single sign-on and a host of other services. They "see" what everyone is using in the sense of which apps users are logging on to. Okta used data from 7,400 customers and more than 6,500 cloud, mobile and web app integrations to compile a new report. The average company deploys more than 150-security focused tools, and based on findings of the past four years, there is a new modern security stack consisting of four layers of security. Those are designated as:
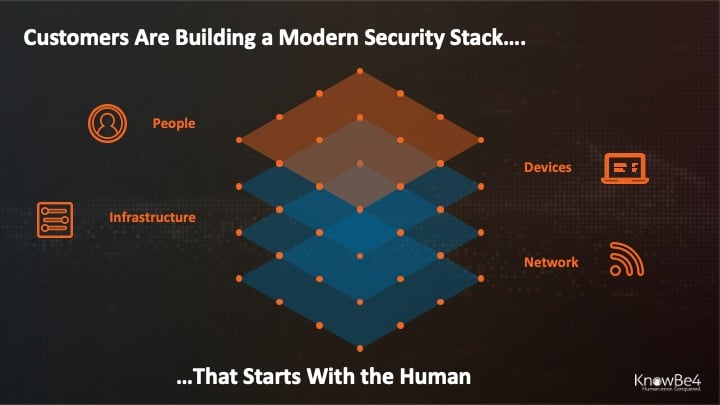
With cybercriminals knowing your untrained users are the weakest link into your network, it is more important than ever to add cyber security awareness training and strengthen that people layer. Today’s email filters have an average 7-10 percent failure rate; and about 30 percent of data breaches are caused by repeat offenders from within the organization. You need a strong human firewall as your last line of defense.

Shifting organizational behavior requires a recognition that simply exposing employees to security-related information will never be enough. Instead, it is imperative to train secure reflexes through intentional and methodical simulated testing so that employees are continually exposed to the situations in which you hope they will exhibit secure behavior.
Some security and organizational leaders might be hesitant to phish their users, fearing that end-users or managers could react negatively to the experience. In fact, some organizations may even have horror stories of phishing simulations that have backfired, resulting in more harm than good. Yet, security leaders, auditors, and adult-learning experts agree that the best way to train secure reflexes is through simulation (not information).
It is possible to work through concerns related to simulated phishing and, in fact, make the experience positive for end-users and management alike. Use the following five principles to build a positive anti-phishing behavior management program:
Creating your anti-phishing behavior management program according to these five principles will ensure that your program is seen as something that builds-up employees rather than tearing them down. These principles are aimed at recognizing that humans can become an effective last line of defense for your organization when given proper training, motivation, and support.
We want you and your employees to enjoy the benefits of a great security awareness training program without experiencing the pain and setbacks associated with missteps. Set your organization up for success by avoiding these common cyber security awareness program fails:
Follow these guidelines to ensure the success of your program. Need help getting started? KnowBe4's Automated Security Awareness Program takes away all the guesswork. Answer 15-25 questions about your goals and organization and get your customized program in just 10 minutes!
* This list is also available as an infographic
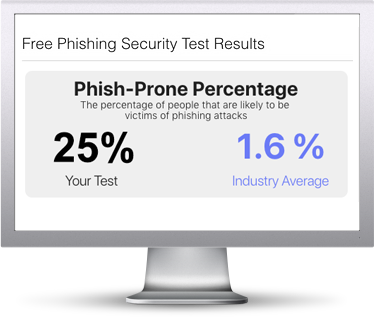
Find out what percentage of your users are Phish-prone™ with your free Phishing Security Test. Why? If you don't do it yourself, cybercriminals will. Plus, see how you stack up against your peers with phishing Industry Benchmarks. Start phishing your users now. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Ask yourself, do you have the capacity and capability and talent within the organization to be able to put out a product that will actually drive quality training and the behavior change you’re looking for? Even organizations that have dedicated internal training teams can struggle with this.
Usually, taking that next step in looking for an outside vendor means you are looking for help with frequency, providing the right kind of content, and the ability to couple that with the correct activities that should be happening like simulated phishing. It can be appealing to do it on your own because you have complete control. However, everything is manual and it’s really hard to be good at (let alone have time for) creating a really robust security awareness program with a good variety of content.
Something to look at as you’re evaluating the market is that potential vendors have content available in a variety of flavors, lengths, languages, role-specific, etc. to fit the needs of different users across your organization. Having ways to repeat the same messaging without using the exact same training is important. Maybe you have a handful of topics you need to reinforce throughout the year. Without having a library of different types of content, the messaging falls flat over the course of a year. A good example of the most effective way to accomplish that would be: have a definitive piece of content that you deliver annually, that is what you use to check the box on compliance requirements. Then you have supplemental content that reinforces the annual training. As you’re looking at vendors, evaluate if they would only be fulfilling the annual training and in that case, necessitate a secondary or tertiary vendor to build up that content library you will need.
5 Ways Vendors Can Help To Improve Your Program:
Reporting
Investing in a program and not having any insight to prove its value is a huge problem. Easy access to reporting data is an absolute necessity. It’s easy to get lost in a ton of metrics, but best to focus on a few areas that show changes in behavior and can consistently be validated through easily accessible tools.
Three key areas to make sure you are covering include: an understanding what is most valuable to measure, having the tools that allow you to easily grab the data you need when you need it, and having a narrative that goes along with the reporting. Most of the time, executives are just seeing high-level numbers with no context. Having a meaningful story is much more effective at illustrating a narrative that shows movement of the behavioral change of an organization.

In this webinar KnowBe4’s Perry Carpenter and Joanna Huisman discuss the benefits of partnering with an experienced provider and what to look for as you evaluate Security Awareness Training vendors.

With so many regulations and audit standards requiring organizations to provide critical security-related information and training programs for their employees, it can be shocking that security leaders often encounter high-level "push back" when seeking to implement cyber security awareness and training programs.
To overcome this situation, propose your program in a way that addresses executive concerns, links to corporate objectives, and tells a story. This is accomplished in three steps:
Habit five of Stephen Covey's "Seven Habits of Highly Effective People" states, "Seek first to understand, then to be understood." Dr. Covey writes,
"If you're like most people, you probably seek first to be understood; you want to get your point across. And in doing so, you may ignore the other person completely, pretend that you're listening, selectively hear only certain parts of the conversation or attentively focus on only the words being said, but miss the meaning entirely. So why does this happen? Because most people listen with the intent to reply, not to understand. You listen to yourself as you prepare in your mind what you are going to say, the questions you are going to ask, etc. You filter everything you hear through your life experiences, your frame of reference. You check what you hear against your autobiography and see how it measures up. And consequently, you decide prematurely what the other person means before he/she finishes communicating."
It is vital to recognize that most business leaders (and end users) simply will not care about security in the same way that a security professional does. People don't care about security for the sake of security alone. What they care about is the result that a sound security strategy can provide and the impacts/risks associated with the lack of a sound security strategy. Use this understanding to inform the methods that you use to engage the organization and business leaders.
"Culture eats strategy for breakfast." - Peter Drucker, Management Consultant, Educator and Author
Communication Strategy is Key
Any time you are presenting data numbers, don’t leave the interpretation up for chance. The ‘what’ is the data, with every ‘what’ comes a so what? meaning what does that data actually mean? and a now what?, or what do we do in light of that information? Any time you have a what, you need to answer the so what and the now what, otherwise you’re leaving one or both of those things up for interpretation and that’s a chance you cannot afford to take. Your communication strategy throughout the whole process is key. You want to tell a memorable story, the moral being you need cyber security awareness training. Use statistics and charts and graphs to support that story.
Capturing Executive Attention
What’s in it for them - Answer the "so what" question. Answer specifically for each member of the executive team what is going to matter most for them with the output of a security awareness training program. This can be talked about positively - increased resiliency that leads to stabilization of environment, higher employee productivity or negatively - pain that can be avoided when this is done right (data doesn’t get exposed, users don’t get compromised, etc.).
Outline clear connections - Showing connection between the action of training and things that are important for that executive. Could be a specific system, business outcome, specific project, a regulation they are accountable for.
Measurement and stories - Talk about what is going to be measured, how it will be presented, and use that to get into the morality (this is what goes wrong without a security awareness program, here is what can go right, etc.)
Be on the Lookout for Ways To:
Use SMARTER Goals
Show that you are being very intentional about starting your program and you will more likely get the support, budget and resources you need to get it started. Use a SMARTER goal-setting framework, goals should be Specific, Measurable, Actionable, Risky, Time-keyed, Exciting and Relevant.
Goals like "The goal is to reduce our phish-prone percentage" or "To be able to engage employees so they are more aware of the risks and threats around them" are not specific or measurable and are certainly not exciting. An example of a SMARTER goal would be: We are going to reduce our phish-prone percentage from an initial baseline of 30% down to 15% within the next 45 days. You will know for sure whether you’ve hit the goal or not once that 45 days is up. With this framework in mind, it is much easier to build out your training plan and reporting schedule around these types of goals.
Brainstorming Worksheet for Gaining Support
We recommend filling something like the below sheet out for each executive you need to get buy-in from. This isn’t to share with anyone, it’s a tool for you to help before you start meeting with your executive team. Find ways to amplify their value proposition and address or minimize their concerns early on. Try to have one-on-one conversations before you officially ask for support so there are no major surprises when that time comes.

It's a Marathon, not a Sprint
It's very important that you present this as an ongoing program from the very beginning - not a one and done. Think about the difference between an event and an ongoing effort… and the difference between a sprint and a marathon. Time and consistency make a BIG impact in changing behavior for the better.

In this webinar, Perry Carpenter, Chief Evangelist and Strategy Office at KnowBe4, helps you detangle the complicated web of politics around securing executive support for security awareness training.
Awareness posters are great to display in the office as a reminder for the whole organization to keep security top of mind. Posters should be changed frequently enough so the message doesn't get stale. These high-res JPGs are suitable for printing:

The Alliance for Strong Families and Communities aimed to train their staff and enrich their security posture. See how KnowBe4's integrated security awareness training and simulated phishing platform helped them to reduce their Phish-Prone Percentage from 36% to 2.2% within 12 months.
“By employing that automated, immediate remediation training, we know that it’s only a matter of time before our PPP is back down to 2%. It’s our job to make sure our people are cognizant and skeptical of threats so they can stay secure, and KnowBe4 is helping us do just that,”
- G.M., Systems Administrator and Supervisor

After an Illinois school district fell victim to a DDoS attack, security and phishing became a higher priority. They needed a better way to protect sensitive data and ensure adherence to The Family Educational Rights and Privacy Act. See how they were able to reinforce cautious vetting of emails amongst staff members with phishing and training campaigns.
“My staff is excellent at teaching, but aren’t as experienced with technology, and they don’t have time in their busy days to gain a better understanding of technology and information security. The KnowBe4 Security Awareness Training model was a way to get their attention and their interest. ‘You just got had with a phishing email’ stands out and would grab anyone’s attention!”
- D.R., CETL, Director of Technology

TXT e-solutions was well aware of of the problems that organizations face with social engineering attacks, which is why they believe that educating employees about the dangers is so important. Given the ISO 27001 compliance requirement, their desire to strengthen the company's security culture and their need to satisfy GDPR compliance requirements, they found KnowBe4 to be the best fit to meet their needs.
“In order to fight an ongoing threat of phishing, we have adopted the KnowBe4 security awareness platform to educate our users about phishing and anti-phishing techniques, use security protection and report suspicious activities. By doing so, we have reduced exposure to fraud and identity theft. The most effective fix to phishing is training and KnowBe4 is the right tool for it. Phishing and training campaigns have proven to be effective; we have fewer users clicking on phishing emails since the beginning. You can easily change the difficulty levels of the email campaigns for your more experienced users. KnowBe4 helps us to raise awareness of social engineering attacks. Great company; good pricing; solid training. Highly recommended.”
- A.U., Group IT Network Engineer
In your fight against phishing and ransomware you can now deploy the best-in-class phishing platform combined with the world's largest library of security awareness training content; including 1000+ interactive modules, videos, games, posters and newsletters. Get access to the full library now!
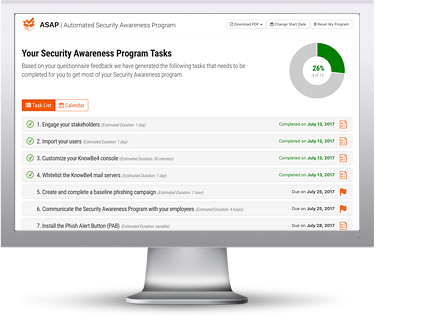
Many IT pros don’t exactly know where to start when it comes to creating a security awareness program that will work for their organization. ASAP allows you to build a customized Security Awareness Program for your organization that will help you to implement all the steps needed to create a fully mature training program in just a few minutes.
 Old-school awareness training never really hacked it. Herding your employees in the break-room, keeping them awake with coffee and donuts and subjecting them to death-by-PowerPoint gave traditional awareness training a bad rap.
Old-school awareness training never really hacked it. Herding your employees in the break-room, keeping them awake with coffee and donuts and subjecting them to death-by-PowerPoint gave traditional awareness training a bad rap.
KnowBe4 is your platform for new-school security awareness training. We help you keep your employees on their toes with security top of mind. With this new-school integrated platform you can train and phish your users, see their Phish-prone percentage™ and their Risk Score improve over time and get measurable results.
Your KnowBe4 subscription gives you access to the world’s largest security awareness training library with always-fresh content, via the unique ModStore.
You can choose from dozens of categories with more than 5,000 real-world, known-to-work phishing templates in 34 core languages (as well as 9 more with limited support) that give you the most realistic phishing test environment available on the market.
Whether you're a small business, enterprise, or are looking to partner with KnowBe4, we will suggest best practices for your size/type of organization!
We have the largest content library in the world. We are the largest security awareness training provider in the world. With over 50,000 customers (and counting), nearly 1,000 employees, and offices in 9 countries, KnowBe4 is the world's most-popular and most proven security awareness vendor.
Keep Users Vigilant About Cybersecurity
Melody was referred to KnowBe4 and immediately began phishing campaigns for her staff, telling only one other partner. Based on initial results, they identified the need for staff training and got buy-in from the rest of their partners. She trains staff to be vigilant about phishing and ransomware attacks and KnowBe4 makes her job easier because of the available resources on the platform.
Why You Need To Invest In Your Human Firewall
Jesse got his CISO involved with KnowBe4 from the beginning and had top-down buy-in. When they started phishing their users they had a 23% click rate. Based on reported results from training and phishing campaigns, they are getting more buy-in from across the organization. He recommends KnowBe4 and thinks not enough organizations invest in the human element of cybersecurity.
How KnowBe4 Helps IT Sleep Better at Night
Nelson is the IT Director for a nonprofit that was hit with a ransomware attack a few years ago. While the attack was caught immediately and they were able to restore their files, they realized they needed help. He phishes users weekly and went from a 33% Phish-prone rate to less than 1%. Since starting KnowBe4, he sleeps better at night and users are constantly aware of cyberattacks.
You and your team have made my life much better in dealing with employee awareness. It is very appreciated and has given us boost up with our regulatory requirements and preventative measures. I love KnowBe4 and if you ever need a reference, feel free to have people contact me.
M.E.SVP/ IT, DR & Security
If you need an advocate on the west coast, just refer people to me…I’m so impressed.
E.J.Senior Manager, Network Operations
Working with you is a breath of fresh air compared to other vendors who refuse to listen to what I ask and respond in kind.
J.C.Vice President, Information Technology
I have been enjoying your product a lot. I also love the brief updates about news and issues from Stu every so often. It helps to keep me informed and aware of any potential threats.
T.Z.IT Support Specialist
We have been using KnowBe4 for a few years now and we are very happy with the service. We love the new features that you have added to the phishing campaigns.
T.M.VP of IT / Information Security Officer
Good Morning, Love, love, love it!! Thank you.
R.B.Director of Information Technology
We love your products. We are happy with using your service. Thank you.
A.S.Senior Systems Engineer
I am a very happy camper, thanks to your excellent and entertaining Kevin Mitnick Security training program, and to our account Rep. Sean Ness, we are loving your product.
D.S.Trainer, Human Resources
It’s going well. Love the ability to track progress and especially love the “auto-nag” feature so I don’t have to remember to send out reminders periodically.
K.S.Chief Information Officer
I couldn’t be any happier. Thank you. I love your service.
H.G.CISA, CRISC, Sr. Security Analyst
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Get a product demonstration of the innovative Kevin Mitnick Security Awareness Training Platform. In this live one-on-one demo we will show you how easy it is to train and phish your users.
Today, your employees are frequently exposed to advanced phishing and ransomware attacks. You need New-school Security Awareness Training.
KnowBe4 is the world’s most popular integrated Security Awareness Training and Simulated Phishing platform.
Your users are your last line of defense. Find out how affordable creating a "Human Firewall" is. Get a quote for your organization now and be pleasantly surprised.

Researchers at IBM X-Force are monitoring several ongoing phishing campaigns by the Russian state-sponsored threat actor ITG05 (also known as “APT28” or “Fancy Bear”). APT28 has been tied to Russia’s military intelligence agency, the GRU.

Analysis of attacks on banking institutions in Canada can be almost perfectly tied to the use and availability of phishing-as-a-service platforms, indicating increased use by threat actors according to new research by Fortra.
© KnowBe4, Inc. All rights reserved. | Legal | Privacy Policy | Terms of Use | Security Statement | Sitemap